Firewall activities
Firewall activities
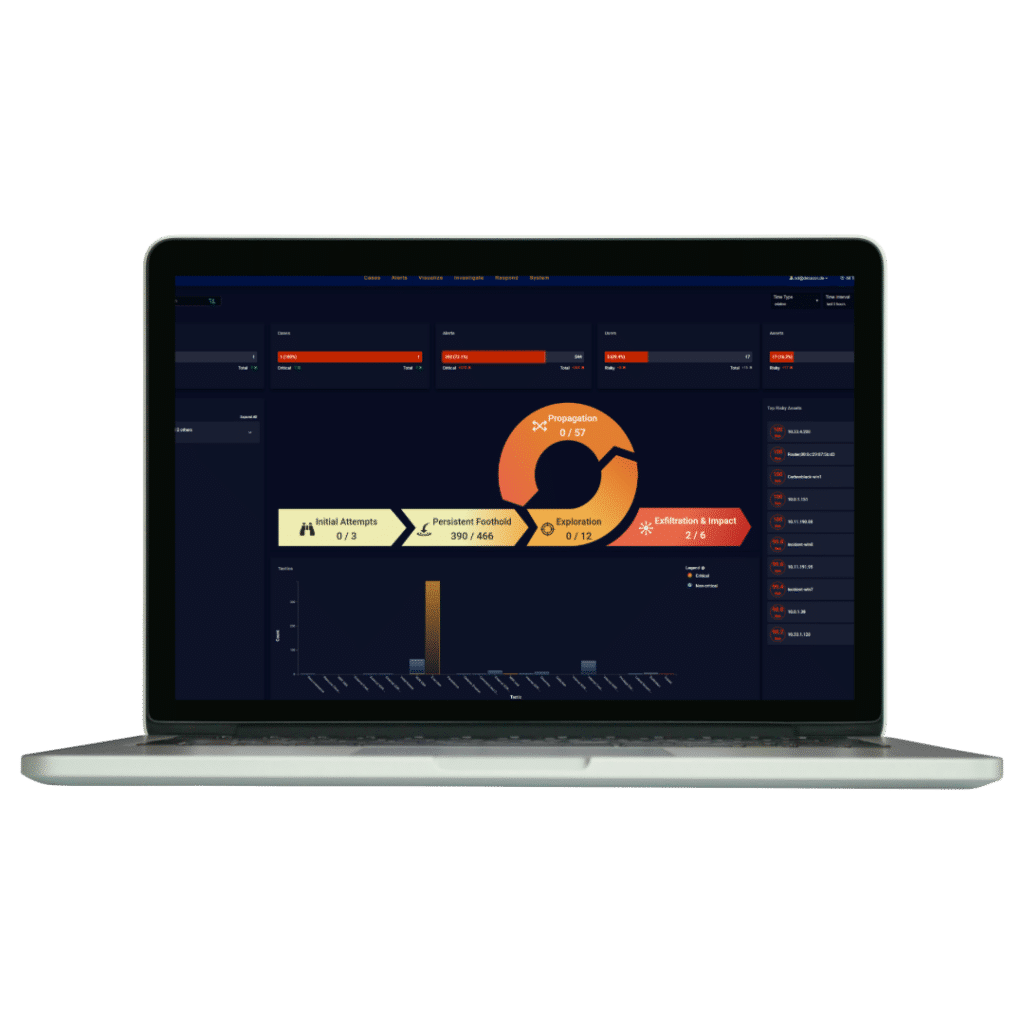
play a crucial role in network security for companies, serving as the first line of defense against cyberattacks. Firewall logs are a treasure trove of information, recording all incoming and outgoing traffic at network boundaries. These logs contain details about allowed and denied connections, such as source and destination IP addresses, ports, protocols used, and precise timestamps for each event.
advanced solutions
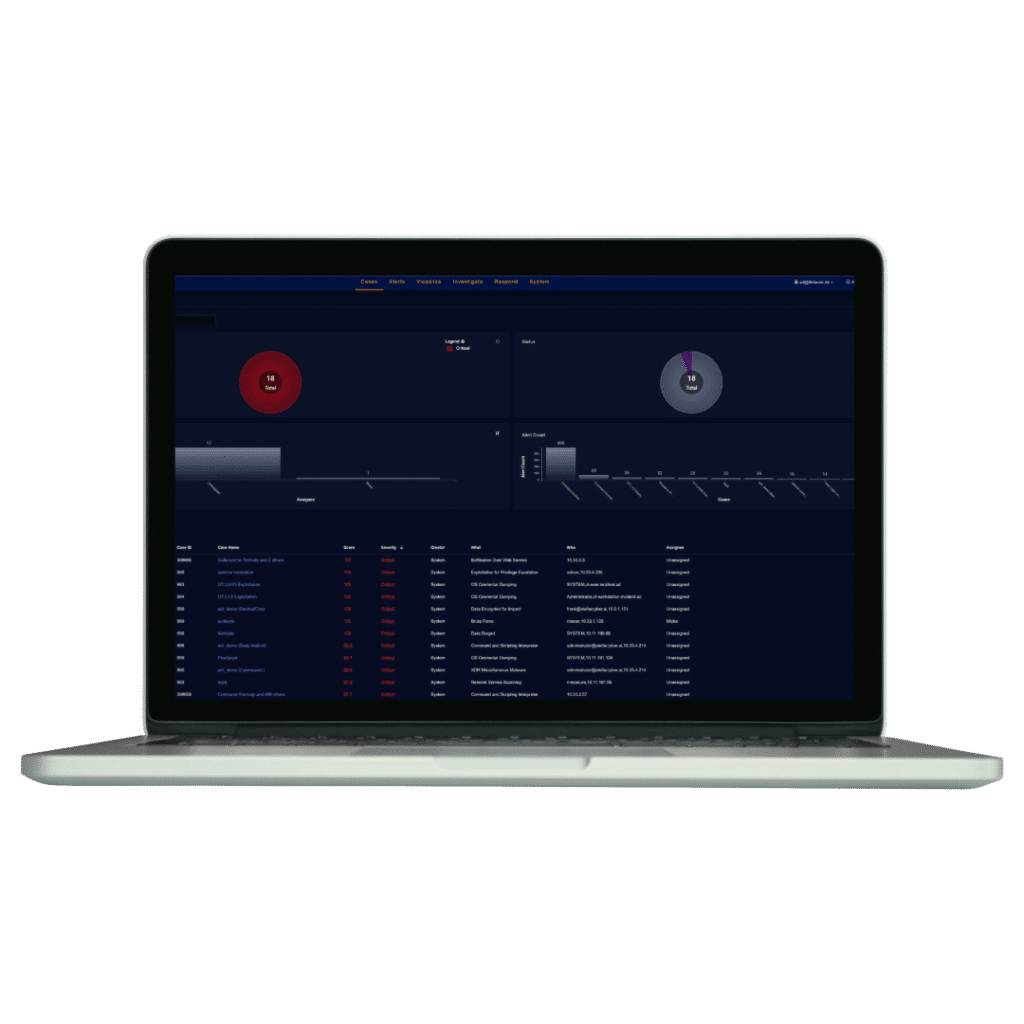
With cyber Inspector’s advanced solutions, organizations can not only monitor firewall logs but also benefit from automated threat detection and real-time log data analysis. The system can identify suspicious activities like brute force attacks, port scanning, or attempts to exploit known vulnerabilities.
proactive measures
cyber Inspector offers proactive measures to protect against unauthorized access and potential attack campaigns through AI-driven monitoring, which means even complex and hidden attack patterns can be detected and addressed before they escalate into serious security breaches. Additionally, detailed reports and notifications are provided, allowing IT departments to respond quickly and effectively when a threat is detected.

cyber Inspector
For companies seeking a tailored solution, cyber Inspector can integrate with existing security infrastructure and support 24/7 monitoring, ensuring that firewall logs are continuously analyzed to catch irregularities. This helps not only in identifying current threats but also in building a strong defense against future attacks.
offers a solution
In short, cyber Inspector offers a solution that not only tracks firewall activities but also ensures that the data is actively used to enhance corporate security and minimize risks.